This case study briefly demonstrates the way to enforce datasource security.
-
As mentioned in the section called “Datasource Security”, to enable datasource security,
a segment of codes in ERS2.xml must be uncommented. The segment of codes is as
follows:
<ers:mbean name="ERS2:name=DSMFactory" class="com.elixirtech.data2.DataSourceManagerFactory"> <ers:property name="DataSourceManagerClassName"> com.elixirtech.ers2.data.SecureRowColDataSourceManager </ers:property> </ers:mbean>
- Start the server. Information about starting up the server can be found in the section called “Starting the Server”. If the server is already started before the editing of ERS2.xml, a restart of server is required.
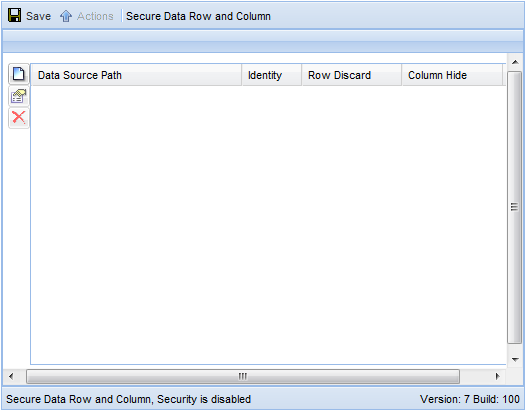
- After log in, go to Administration, then Data. A screen as seen in Figure 5.3, “Datasource Security” will be loaded. If the codes are still commented in ERS2.xml, or a the server is not restarted after the editing, at the bottom of the page, it will say Secure Data Row and Column, Security is disabled.
-
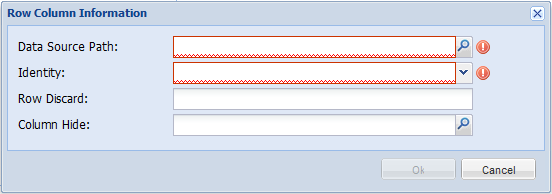
Click on the Add icon to add a new restriction. A window like in
Figure 5.4, “Row Column Information” will appear.
- DataSource Path
- User enters or selects the path of the datasource. This field is compulsory.
- Identity
- Specifies the user or group that is being restricted. Similar to DataSource Path, this field is compulsory.
- Row Discard
- Discards a particular row. Filter rules such as "<",
">", "<=", ">=", "=", "!=", "~" and "!~" are supported. For example,
using FruitSales.ds to demonstrate, to discard row(s)
that contains
Applein theFruitcategory, enter the following in the field:Fruit=Apple
When the restricted user or group views this datasource, any row(s) that contains
Applewill not be loaded. - Column Hide
- Hides a particular column from the selected user
-
Click on
Okto confirm the configurations. Click onSaveto save all configurations done, else all editing will not be saved. -
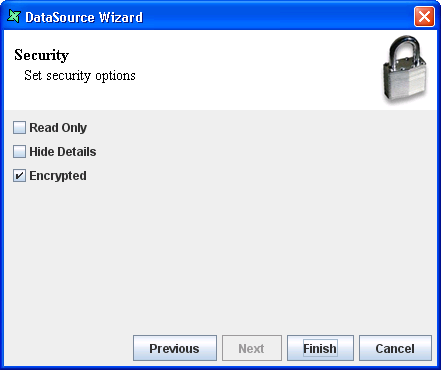
It is recommended that a datasource is encrypted if it contains sensitive
data. This is because the restrictions would not apply if a datasource is being
copied from one directory to another. On the other hand, an encrypted file
retains the encryption properties even after being copied to another directory.
This can be done in the last page of the DataSource Wizard by checking
Encryptedas seen in Figure 5.5, “Encrypt DataSource”.