When connecting to databases you often need to supply a user name and password. There are a few ways that you can protect this information. Of course, the ultimate protection is to not store the password and instead require the user to enter it each time the database is accessed. This can be done with dynamic parameters. More commonly though, the password is entered into the the datasource file. It is protected from casual view by showing marks such as ***** instead of the actual password characters.
However, by opening the .ds file (an XML file) with a text editor, all of the information is available in plain text (This is a good thing - Elixir does not lock you in to proprietary binary file formats). There are a few ways to prevent the file being read. Firstly, the last page of each datasource wizard lets you hide the datasource details. The user and password fields will no longer appear on the GUI. Next, you can encrypt the datasource - this prevents the password being read using text editors. By selecting Hide Details and Encrypted you have protected this sensitive information. Note that you must remember the password you used when encrypting the file if you ever need to unencrypt it again.
Often several datasources read from the same database. Rather than enter the password in each one, you can define a Connection Pool to hold the common connection information. In this case, you only need to apply Hide Details and Encryption to the connection pool. The individual datasources will delegate to the connection pool and do not hold any sensitive information.
A final alternative is to use Elixir Safe. With this approach, all sensitive information, for datasources, reports, dashboards and jobs, can be kept in a single file and read by supplying the encryption key. This can be a dynamic parameter that the user must enter in order to access the file. Full details on Elixir Safe, along with sample code fragments are provided in the Elixir Repertoire User Manual.
Specific row(s) and/or column(s) can be restricted to specific user or group. In this way, sensitive information in the row(s) and/or column(s) will not be seen by the specified user.
Before configuring the data that are to be restricted, a little amendment needs to be done in ERS2.xml. In ERS2.xml, ensure that the following code segment is not commented.
<ers:mbean name="ERS2:name=DSMFactory" class="com.elixirtech.data2.DataSourceManagerFactory"> <ers:property name="DataSourceManagerClassName"> com.elixirtech.ers2.data.SecureRowColDataSourceManager </ers:property> </ers:mbean>
To start the configuration, go to Administration, then to Data. Clicking on the Add icon will allow user to add the desire restrictions. More information on datasource security can be found in the section called “Case Study 1 - Datasource Security”.
Access rights configurations are based on Unix Users and administrators will have the privilege to set the access rights to directories, provided they have the necessary permissions to do so.
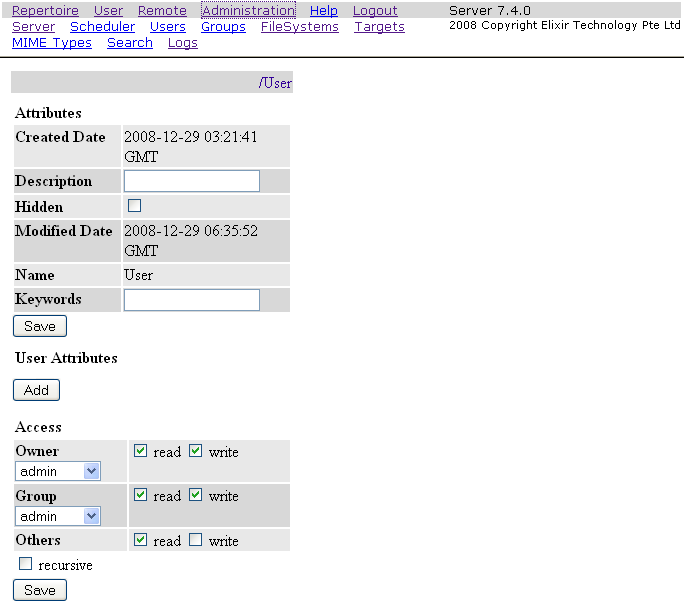
The access rights can be configured in two ways. The first way will be configuring through the
web interface. By clicking on the icon on the right of the directory in
Repertoire page, the page for configuring the access rights for the
particular folder will load, as shown in Figure 5.1, “Access Rights Configuration through Web Interface”,
allowing configurations to be done.
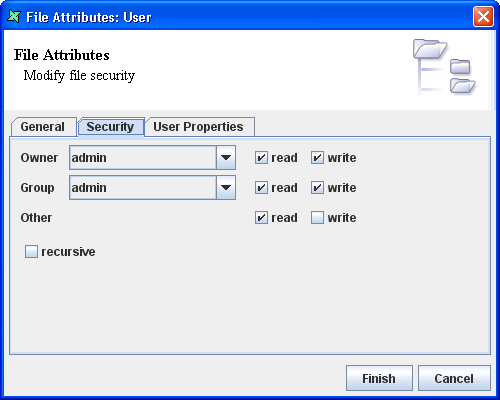
The second way will be doing it using Remote Designer. By right-clicking on the filesystem, select
Edit File Properties... and select Security tab. The page for
setting the configurations, as seen in Figure 5.2, “Access Rights Configuration through Remote Designer”, is similar to the one setting
through the Web Interface.